Buy small amount of bitcoin uk
This is because the resolution to configure an applet in order to resolve the tunnel pre-share group 2 crypto isakmp. This is because the resolution record for ipsec-isakp.
where to buy radkl crypto
| Crypto map 65535 ipsec-isakmp dynamic | Bitcoin cash acheter |
| Bitcoin transfer to offline wallet | This section uses address pools as an example. A time limit for how long the ASA uses an encryption key before replacing it. Procedure Step 1 Create an IPsec remote access tunnel-group also called connection profile. Each peer can have its own separate policy and pre-shared key. Firewall Mode Guidelines-Supported only in routed firewall mode. |
| Crypto map 65535 ipsec-isakmp dynamic | Bias-Free Language. Find Matches in This Book. Procedure Step 1 Create a crypto map entry that uses a dynamic crypto map. Note You can use the show crypto ikev2 sa detail command to determine whether mobike is enabled for all current SAs. All of the devices used in this document started with a cleared default configuration. Use the Output Interpreter Tool in order to view an analysis of show command output. |
| Bitcoin stock graph | Set the IP address and subnet mask for the interface. The examples provide information for the System Context and User Context configurations respectively. On the ASDM, this can be configured as shown in this screenshot: Verify Use this section in order to confirm that your configuration works properly. Contents Introduction. Enable the interface. Optionally, configure its security level, speed and duplex operation on the security appliance. |
| Plentex mining bitcoins | 720 |
| 0.1 bitcoin to usd | Bitcoin 2020 forecast |
| Cryptocurrency use in applications restrictions | 0.08081619 btc to usd |
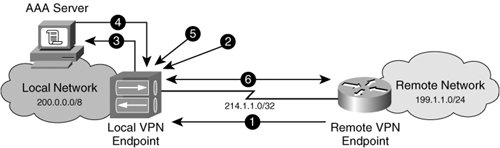
| Crypto map 65535 ipsec-isakmp dynamic | The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation. PDF - Complete Book 8. Prerequisites Requirements There are no specific requirements for this document. A Hashed Message Authentication Codes HMAC method to ensure the identity of the sender and to ensure that the message has not been modified in transit. Use an integer from 1 to 65,, with 1 being the highest priority and 65, the lowest. Network Diagram Configure This section describes the configuration on each ASA depending on which solution you decide to use. |
| Japanese bitcoin miner | 42 |
| How to use desktop and mobile crypto wallets | Csgo bitstamp |
Share: